From Part I, you have finished install ISA Server 2006. Before using the server, you need to do some configurations first. On Getting Started with ISA Server 2006 page on ISA Server Management, there are 5 steps for set up ISA Server as the figure below.
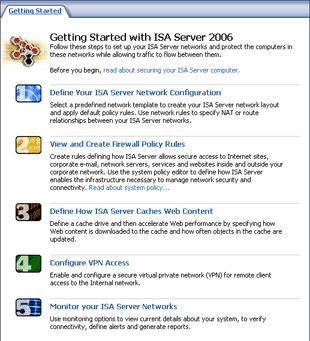
To use ISA Server, only first 2 steps on the figure above are needed to be configured so this part will shows how to configure Network Topology on ISA Server which is the first step in the figure above. For the second step, I will cover in the next part(part III). Also, you need to enable client to access ISA Server by configure on clients,too. Client Configuration will be covered in part IV.
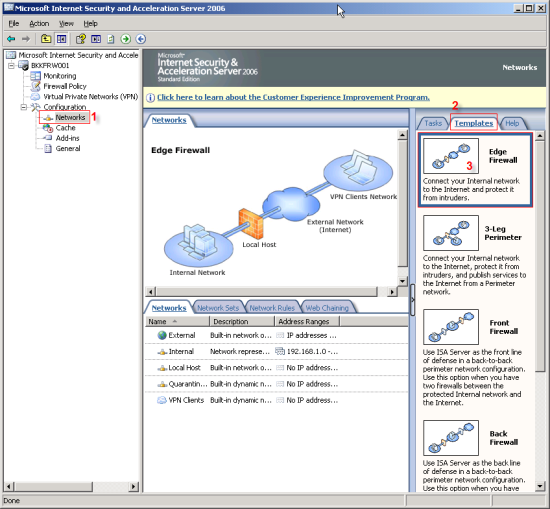
ISA Server 2006 comes with many defined templates. Here are some details of each template. You can select one of them that match your network.
1. Edge Firewall:
This is a standard network topology for small to medium organization. The ISA Server is a main gateway controlling traffic between intranet and internet. The ISA Server needs 2 network interfaces
2. 3-Leg Perimeter:
This is a standard network topology for medium to large organization. There are another network which is Perimeter network adding to ISA server compare to edge firewall. The perimeter network or DMZ (Demilitarized Zone) is a network that is less secure for serving Web server, E-Mail server, DNS server,etc so that internet users can access these services without access to internal network. The ISA Server needs 3 network interfaces.
3. Front Firewall:
This is a network topology for organization that security is high priority. In this case, there are more than 1 firewall server. When hacker attacks the server and one fails, there is still back firewall to protect your internal network. This template, ISA Server will be act as front firewall server between internet and perimeter network and needs 2 network interfaces.

4. Back Firewall:
This is a network topology for organization that security is high priority. The configuration is the same as in Front Firewall template except that the ISA Server that you’re configuring is the back firewall that serperate internal and perimeter network.This template, ISA Server needs 2 network interfaces.
5. Back Firewall:
This is a network topology for organization that security is high priority. The configuration is the same as in Front Firewall template except that the ISA Server that you’re configuring is the back firewall that serperate internal and perimeter network.This template, ISA Server needs 2 network interfaces.

Note: For Front and Back Firewall templates, you have more than one firewall servers. It is best practice that you should use different firewall software or using hardware firewall with software firewall not the same on front and back. If hacker can destroy the front firewall, you still have back firewall which the hacker can’t use the previous technique to attack the firewall.
Step-by-step:
This example will configure ISA Server 2006 using Edge Firewall template.
1. Open ISA Server Management.
1. On left window, expand Configuration and select Networks
2. On right window, select Templates tab.
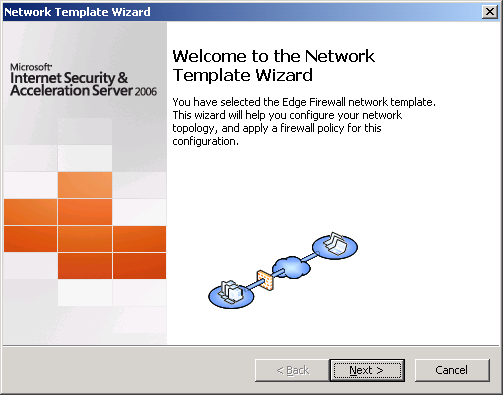
3. Click on Edge Firewall template. Network Template Wizard window appears.
* Click Next.
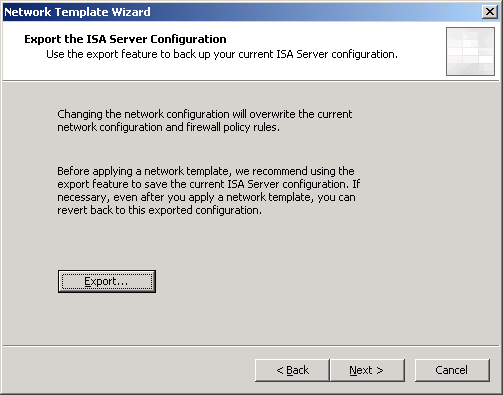
* You can export your configurations before let the wizard overwrite the old one by click on Export button. Otherwise, click Next.
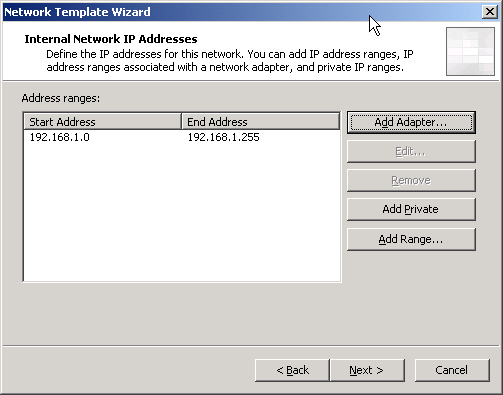
* On Internal Network IP Addresses, you can configure your internel network IP Address. If the existing value is correct, click Next.
* On Select a Firewall Policy, you can select firewall policy template. The description will display what will be configure on ISA Server. I select “Block all” to block all traffic between ISA Server. I will configure rules later in the the next part.
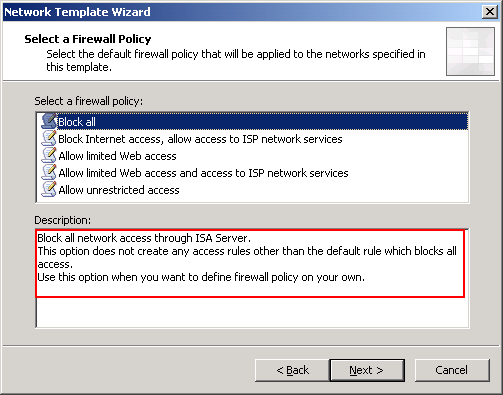
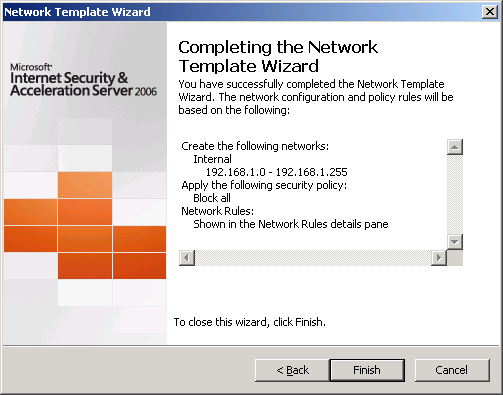
* Click Finish to complete the wizard.
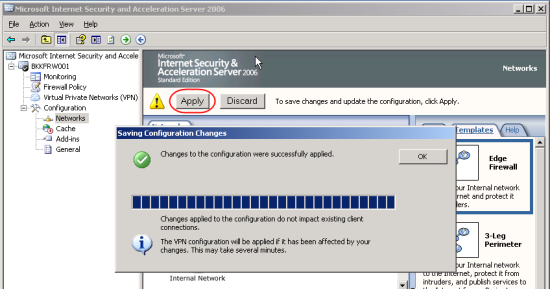
* To make ISA Server takes effect, click on Apply.
No comments:
Post a Comment